Security teams across the globe have been scrambling to address a dangerous new zero-day vulnerability in a popular Apache logging system. In this article, I am trying to explain the Apache Log4J security vulnerability in plain English. Log4J is a popular Java library that can be used for logging code. You can log error messages and…

Zero Trust for Insider Threat
Traditional IT network security is based on the castle-and-moat concept. In castle-and-moat security, it is hard to obtain access from outside the network, but everyone inside the network is trusted by default. This strategy focuses on securing the castle (or sensitive system) from external threats while placing minimal controls on trusted insiders. The core principal…

What is the castle-and-moat network model?
“Castle-and-moat” is a network security model in which no one outside the network is able to access data on the inside, but everyone inside the network can. Imagine an organization’s network as a castle and the network perimeter as a moat. Once the drawbridge is lowered and someone crosses it, they have free rein inside the castle…

What is Zero Trust security?
Zero Trust security is an IT security approach that involves tight identity verification for everyone wanting to access resources on a private network, whether they are inside or outside the network perimeter. Although ZTNA is the most commonly linked technology with Zero Trust architecture, Zero Trust is a comprehensive approach to network security that includes…

What is Cyber security
Cyber security is the practise of defending against malicious attacks or unauthorized access to computers, mobile devices, electronic systems, networks, and data. Cyber security can also be referred to as security for information technology. Importance of Cyber security Cyber security is critical since vast quantities of data on computers and other devices are collected, processed,…

Securing your Salesforce application with IBM Security Verify
Software applications play an important role in our lives. Whether it is in the home or workplace, we use them for communicating with people, staying up-to-date with the things happening in the world, keeping entertained, doing work and much more. Salesforce is a cloud computing service as a software (SaaS) company that specializes in customer…

Work Securely with Your Partners and Contractors
In today’s modern era, it is very common for enterprises to work with contractors and business partners. This brings a variety of users from outside the network. These users are known broadly as the extended enterprise. Though the extended enterprise can be critical in enabling organizations to scale their business, it also brings massive risks…
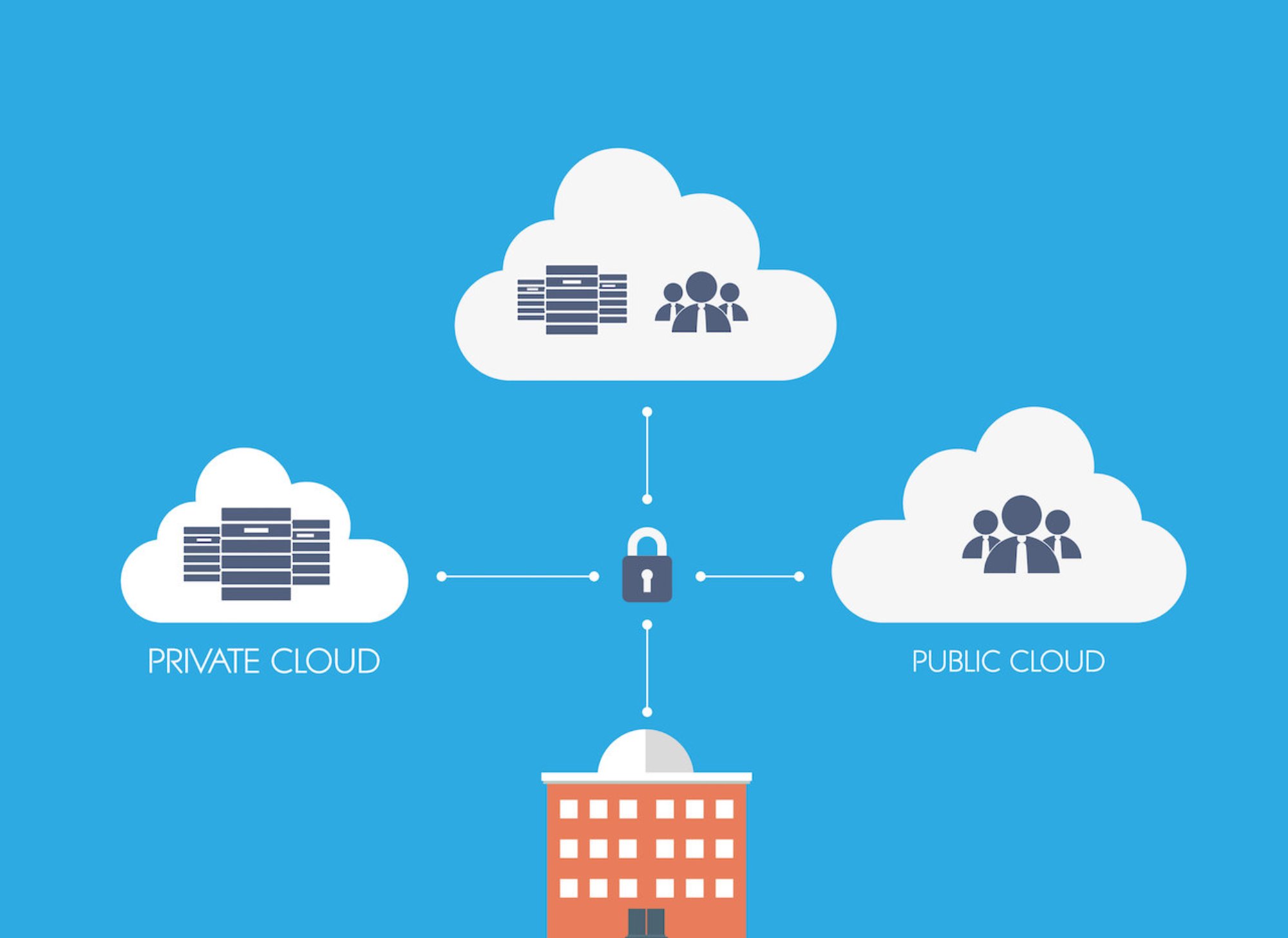
What is Cloud Access Security Broker (CASB)
A Cloud Access Security Broker (CASB) is a software tool or service that sits between an organization’s on-premises infrastructure and a cloud provider’s infrastructure. A CASB acts as a gatekeeper, allowing the organization to extend the reach of their security policies beyond their own infrastructure. CASBs work by ensuring that network traffic between on-premises devices…

AuthN & AuthZ
AuthN and AuthZ are very commonly used terms but are confusing to a novice computer user. So trying to explain with example. AuthN – Authentication is establishing the your identity. AuthZ – Authorization is establishing your privilege Authentication is the process of verifying who you are and making sure you are who you say you…

Administrator Credentials: High Impact Security Breach
When you think about enterprise data security, the first thing you picture is an outside intruder. It might be some kid in a dark basement hacking into your servers, or maybe a more sophisticated attack from a cyberspy contingent overseas. However, one of the greatest threats to your enterprise data security stance might be sitting…

Are You Using Jenkins the Right Way?
Jenkins is a popular open source tool to perform continuous integration and build automation. The basic functionality of Jenkins is to execute a predefined list of steps, e.g. to compile Java source code and build a JAR from the resulting classes. The trigger for this execution can be time or event based. For example, every 20…
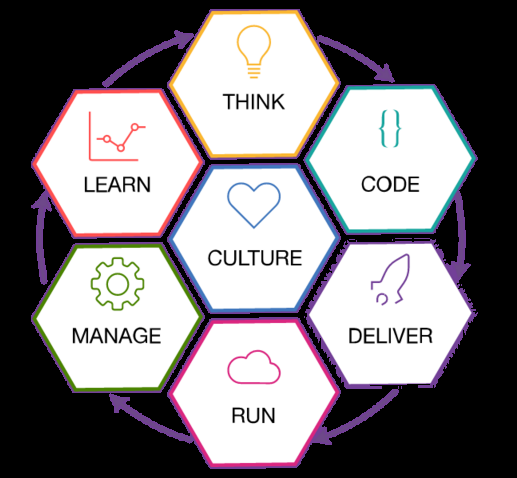
What is DevOps
There are many definitions of the word “DevOps.” Is it a movement? A new process or technology? A job title? Or just a way of thinking? DevOps is a combination of software development and operations—and as its name suggests, it’s a melding of these two disciplines in order to emphasize communication, collaboration, and cohesion between…
How to configure SSO with Salesforce using IBM Cloud Identity Connect
This guide describes detailed steps for configuring SAML 2.0 federated single sign-on using predefined connector between IBM Cloud Identity and Salesforce. For this federation configuration, IBM Cloud Identity acts as Identity Provider (IDP). Salesforce acts as Service Provider (SP). Following are the high level steps for configuring SSO between IBM Cloud Identity and Salesforce: Configure…

Getting started with IBM Cloud Identity Connect
IBM allows you to create a a 30 days trial account for IBM Cloud Identity Connect. If you are already leveraging one of the other IBM Cloud products then you can enjoy IBM Cloud Identity Connect for one year. How to create a new account for IBM Cloud Identity Connect – Go to IBM Marketplace…

IBM Cloud Identity
In an effort to help speed cloud adoption across the enterprise, IBM released a new identity management solution on June 15, 2017 that simplifies employee access to business applications across a hybrid cloud environment. IBM Cloud Identity Connect is designed for managing how employees gain access to their preferred business applications. It is a new…

IDaaS Vendors to Watch
Gartner analysts predict that by 2020, 40 percent of IAM purchases will use IDaaS delivery model, a two-fold increase from less than 20 percent today. Perhaps more important is that 40 percent of those IDaaS implications will entirely replace on-premises IAM implementations, according to Gartner. Future, is in the cloud. Here are the top IDaaS…

What is Identity as a Service (IDaaS)
What is IDaas? Identity as a Service (IDaaS) is cloud-based authentication operated by a third-party provider. The X-as-a-service model means some feature (X) is being delivered or served through a remote connection from a third-party provider, as opposed to a feature being managed on site and by in-house personnel alone. Very simple and day to…
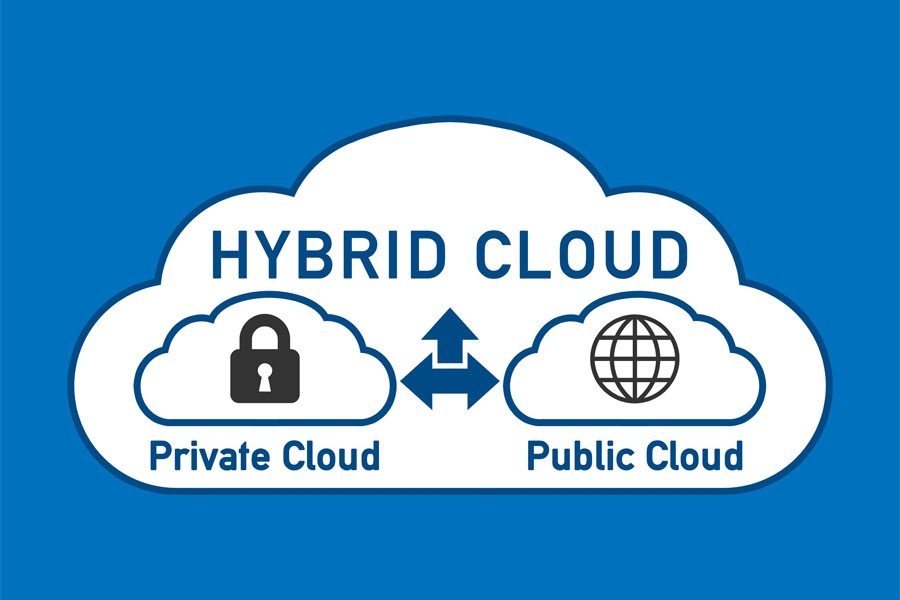
What is Hybrid Cloud?
As the name indicates, it is the functional combination of both public and private clouds. A public cloud like Microsoft Azure leverages the shared chunks of networking infrastructure, computing and its storage which are rented on a specific time basis for the customers. A private cloud comes with the same components but will be restricted…
